Ghost protocol might remind you of a famous blockbuster starring Tom Cruise, but here it applies to a new proposal by the Government Communications Headquarters (GCHQ) in the United Kingdom.
The GCHQ is the British equivalent of the United States National Security Agency, and the proposal’s function is to give law enforcement power to listen in on encrypted communications (like those on WhatsApp, for example).
It’s not the first time the British government has taken aim at encrypted communication: in 2017, then Home Secretary Amber Rudd called for end-to-end encryption to be banned, claiming “real people” don’t need it. Rudd’s comment reflected tremendous ignorance about how modern communication works.
The proposal, referred to informally as ghost protocol, is a more strategic attack on privacy, packaged in security rhetoric that hides technical, personal and societal implications. In an open letter to GCHQ, 47 signatories — including Apple, Google and WhatsApp — have urged the agency to abandon its plans.
How end-to-end encryption works
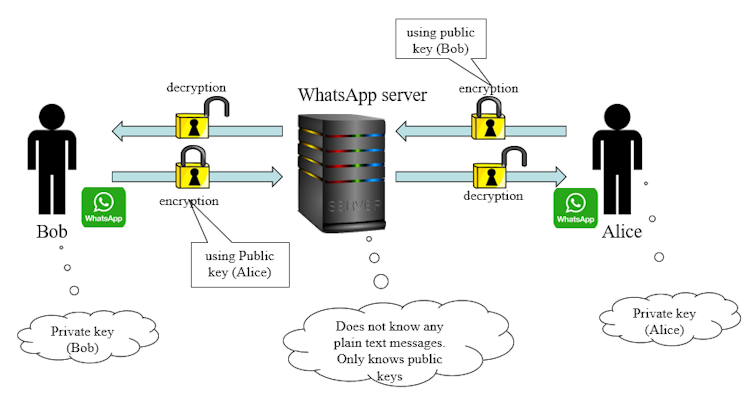
The government proposal says “you don’t even have to touch the encryption” to implement ghost protocol. End-to-end encryption works by generating a pair of public and private keys for each user. Text encrypted using the public key can only be decrypted using the private key, and vice versa.
Hence, if Bob and Alice want to have a chat, both share their public keys and keep their private keys secret. Bob encrypts messages using Alice’s public key (so only Alice can decipher them), and Alice encrypts messages using Bob’s public key.
In a group chat between Alice, Bob, and Jill, every message Alice sends is encrypted using Bob’s public key (to Bob) and Jill’s public key (to Jill). Alice is notified by the app that each message has two recipients. This means that the messaging service’s servers only see public keys and encrypted text: they cannot decipher text, even at the request of law enforcement.
How end-to-end encryption works.
Ghost in the machine
Ghost protocol gets around this problem by proposing that law enforcement can be added as an invisible participant to a conversation. Alice, in conversation with Bob, would then encrypt every message twice, using both Bob’s public key and the public key for law enforcement. Alice would be unaware of law enforcement’s ability to access her conversation.
Framing this as an action that could only be taken if legally approved and only in situations where there is sufficient evidence to justify it sounds reasonable, but ghost protocol completely disregards the many technical implications of modifying software to support a ghost user.
It would require messaging apps to change how keys are negotiated among participants, adding complexity and therefore increasing the potential for security vulnerabilities.
By requiring apps to hide participants, it would undermine authentication mechanisms, introducing new potential vulnerabilities and eroding user trust in the service.
It would also effectively create a backdoor that could be exploited by messaging apps themselves — for example, a company employee who wants to stalk a co-worker. This would create a single point of failure: should a malicious attacker hack into the messaging app system, they would then be able to inject themselves as a silent listener into any conversation.
Social implications
The personal and societal implications are even more serious. Messaging apps would need to update their software to support ghost protocol. Would this update affect all users, regardless of geographical location? Would a Canadian user be affected because a messaging app update implements U.K. law? This opens the door to any government, including dictatorships, to spy on their citizens effortlessly and covertly.
Remember the Edward Snowden leaks?
If two versions of the software existed — one for users in the U.K., one for everywhere else — how would these inter-operate? Would a Canadian visiting the U.K. be able to use the messaging app? Probably not, without an update that incorporates ghost protocol. That update that would remain on their phone after they returned home.
Law enforcement definitely needs access to information to provide security and prosecute crimes, and technology has certainly made this more challenging. But law enforcement’s intelligence-gathering capabilities cannot be supported by undermining individuals’ right to privacy, which is what ghost protocol proposes. It makes the many more vulnerable, so the U.K. can spy on a few.



 AMD Shares Slide Despite Earnings Beat as Cautious Revenue Outlook Weighs on Stock
AMD Shares Slide Despite Earnings Beat as Cautious Revenue Outlook Weighs on Stock  Nvidia Nears $20 Billion OpenAI Investment as AI Funding Race Intensifies
Nvidia Nears $20 Billion OpenAI Investment as AI Funding Race Intensifies  TSMC Eyes 3nm Chip Production in Japan with $17 Billion Kumamoto Investment
TSMC Eyes 3nm Chip Production in Japan with $17 Billion Kumamoto Investment  Supreme Court Tests Federal Reserve Independence Amid Trump’s Bid to Fire Lisa Cook
Supreme Court Tests Federal Reserve Independence Amid Trump’s Bid to Fire Lisa Cook  OpenAI Expands Enterprise AI Strategy With Major Hiring Push Ahead of New Business Offering
OpenAI Expands Enterprise AI Strategy With Major Hiring Push Ahead of New Business Offering  Panama Supreme Court Voids Hong Kong Firm’s Panama Canal Port Contracts Over Constitutional Violations
Panama Supreme Court Voids Hong Kong Firm’s Panama Canal Port Contracts Over Constitutional Violations  Norway Opens Corruption Probe Into Former PM and Nobel Committee Chair Thorbjoern Jagland Over Epstein Links
Norway Opens Corruption Probe Into Former PM and Nobel Committee Chair Thorbjoern Jagland Over Epstein Links  Sony Q3 Profit Jumps on Gaming and Image Sensors, Full-Year Outlook Raised
Sony Q3 Profit Jumps on Gaming and Image Sensors, Full-Year Outlook Raised  SpaceX Seeks FCC Approval for Massive Solar-Powered Satellite Network to Support AI Data Centers
SpaceX Seeks FCC Approval for Massive Solar-Powered Satellite Network to Support AI Data Centers  CK Hutchison Unit Launches Arbitration Against Panama Over Port Concessions Ruling
CK Hutchison Unit Launches Arbitration Against Panama Over Port Concessions Ruling  SpaceX Updates Starlink Privacy Policy to Allow AI Training as xAI Merger Talks and IPO Loom
SpaceX Updates Starlink Privacy Policy to Allow AI Training as xAI Merger Talks and IPO Loom  SoftBank and Intel Partner to Develop Next-Generation Memory Chips for AI Data Centers
SoftBank and Intel Partner to Develop Next-Generation Memory Chips for AI Data Centers  Google Cloud and Liberty Global Forge Strategic AI Partnership to Transform European Telecom Services
Google Cloud and Liberty Global Forge Strategic AI Partnership to Transform European Telecom Services  Nvidia CEO Jensen Huang Says AI Investment Boom Is Just Beginning as NVDA Shares Surge
Nvidia CEO Jensen Huang Says AI Investment Boom Is Just Beginning as NVDA Shares Surge  FxWirePro- Major Crypto levels and bias summary
FxWirePro- Major Crypto levels and bias summary